Response Operation Collection Kit
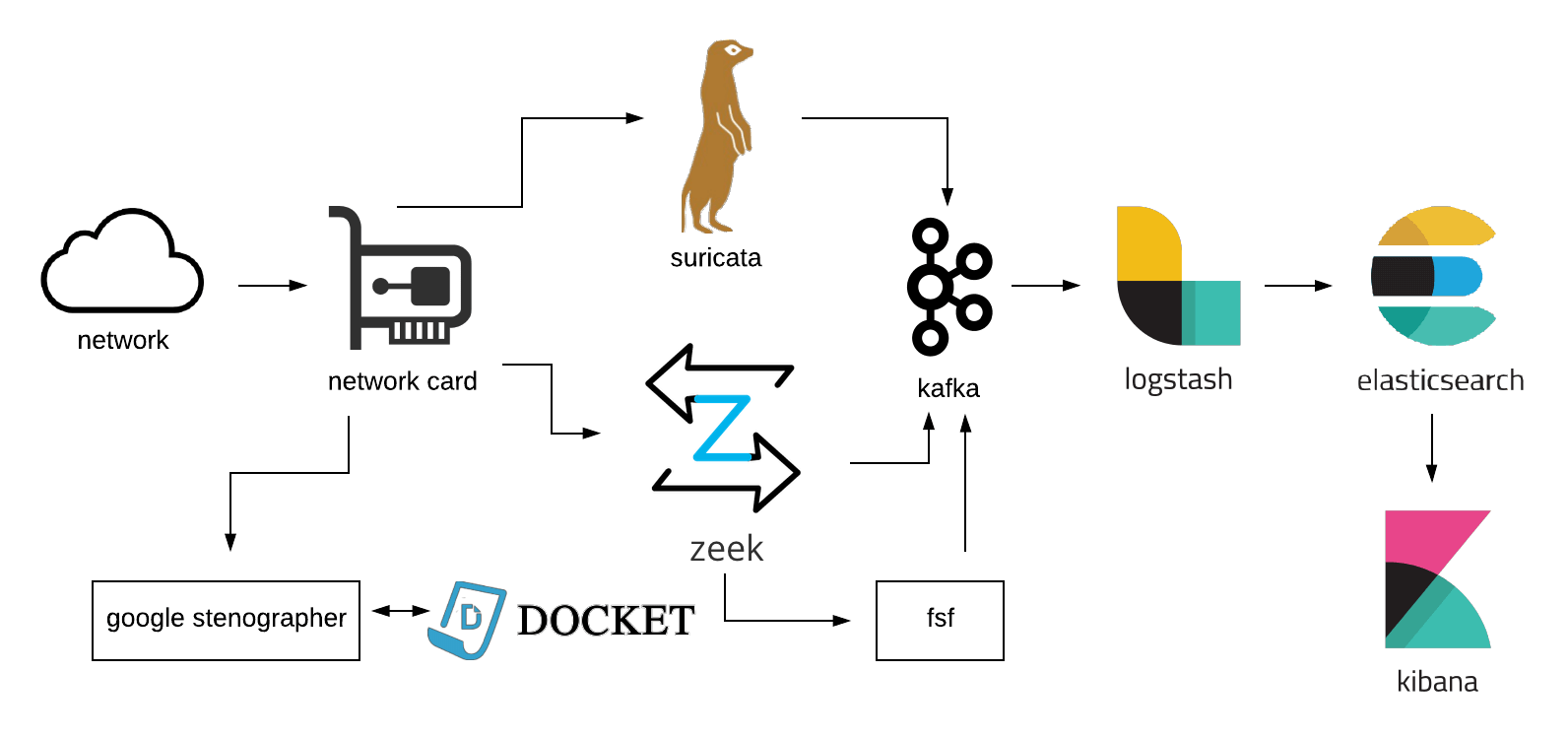
ROCK is a collections platform, in the spirit of Network Security Monitoring by contributors from all over industry and the public sector. It's primary focus is to provide a robust, scalable sensor platform for both enduring security monitoring and incident response missions. The platform consists of 3 core capabilities:
- Passive data acquisition via AF_PACKET, feeding systems for metadata (Zeek), signature detection (Suricata), and full packet capture (Stenographer).
- A messaging layer (Kafka and Logstash) that provides flexibility in scaling the platform to meet operational needs, as well as providing some degree of data reliability in transit.
- Reliable data storage and indexing (Elasticsearch) to support rapid retrieval and analysis (Kibana) of the data.
Features
- Full Packet Capture via Google Stenographer and Docket.
- Protocol Analysis and Metadata via Zeek.
- Signature Based Alerting via Suricata.
- Recursive File Scanning via FSF.
- Message Queuing and Distribution via Apache Kafka.
- Message Transport via Logstash.
- Data Storage, Indexing, and Search via Elasticsearch.
- Data UI and Visualization via Kibana.
- Security - The system is developed and tested to run with SELinux enabled.
Governance and Direction
In 2019, a group of RockNSM creators and contributors formed the RockNSM Foundation to guide the development of RockNSM, and to be stewards of the project. In March of 2019, the RockNSM Foundation was officially registered in the state of Nebraska. The 501(c)3 paperwork has been filed with the IRS to make the RockNSM Foundation an official non-profit. The goal is to keep the intellectual property and future development of the RockNSM project free and open for anyone who wants to use it, and to protect it from outside influence.
THANKS
This architecture is made possible by the efforts of an ever-growing list of amazing people. Look around our Github to see the whole list.
Approach
The Ansible playbook that drives this build strives not to use any external roles or other dependencies. The reasoning behind this is to make the rock playbook a "one-stop" reference for a manual build. This allows users to use the build process as a guide when doing larger scale production roll outs without having to decipher a labyrinth of dependencies.
Templated config files have comment sections added near key config items with useful info. They don't all have it, but they get added as remembered.
